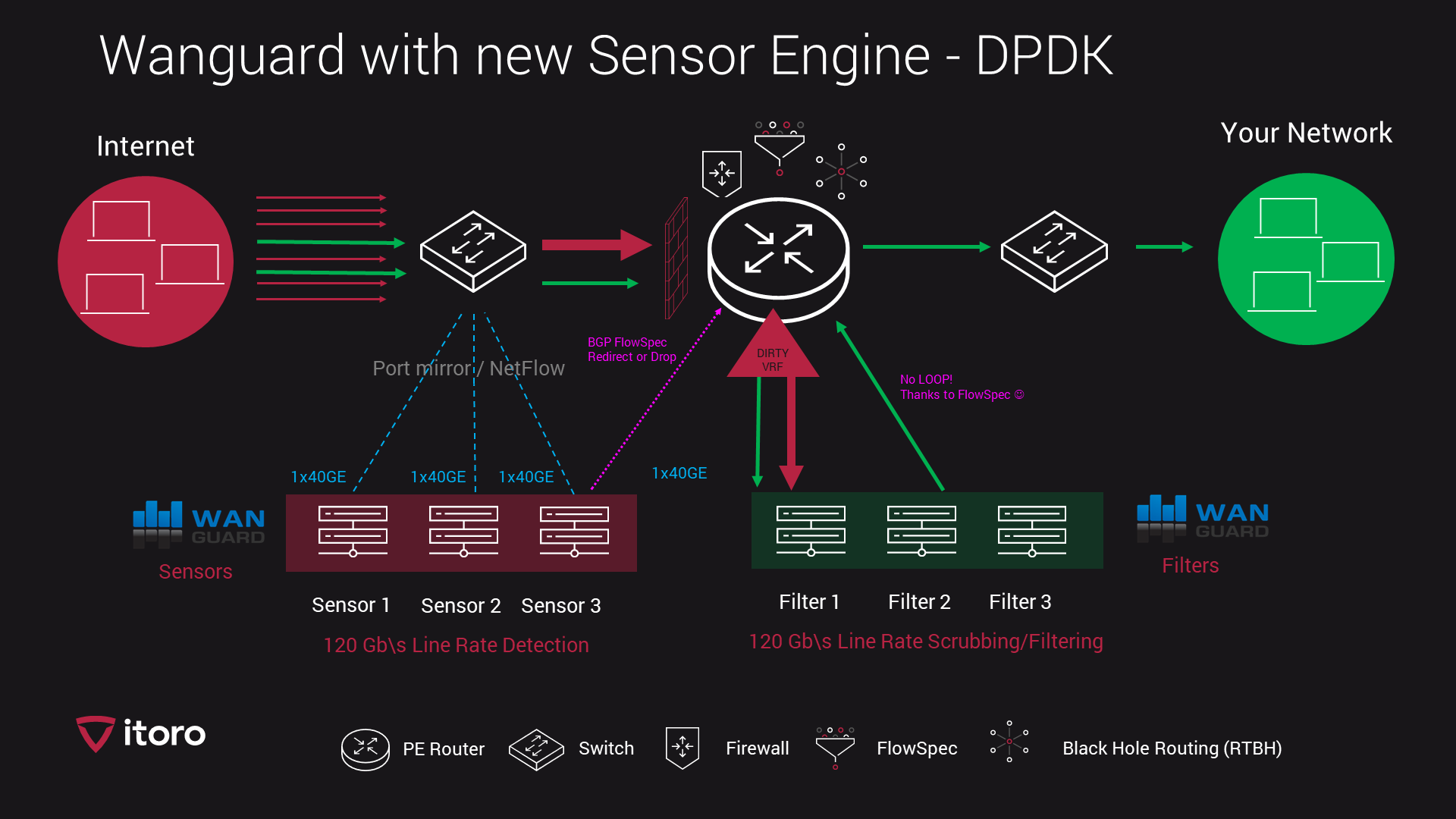
One of Our latest installation - 120Gb\s traffic, RTBH with filtering. Installation was based on Juniper MX204 router.
I would like to present our latest installation with latest Wanguard DPDK engine.
Customer:
Internet Service and Datacenter provider had contacted ITORO to prepare a quotation for 100 Gb\s DDoS solution.
The network had Juniper switches and two Juniper MX204 routers - capable of 4x 100 Gb\s. Due to many short and bursty DDoS attacks, we have chosen a port mirror approach rather than a JFLOW/IPFIX.This allowed for 4 seconds of detection and mitigation, compared to 60+ seconds of detection and mitigation based on any other xFLOW method.
Scenario:
Since Juniper has BGP FlowSpec feature, we have used this for two main purposes.
First - a FlowSpec redirection of attacked prefix to a DIRTY VRF which is pointing to a Scrubbing center with 3x 40 GE capable filters for fine filtering.
Second - a FlowSpec firewall to drop or rate limit any DDoS amplified traffic directed to the network. FlowSpec is able to drop almost 80% off DDoS amplified UDP floods, leaving our Filter cluster of 3 servers almost nothing. Since some smaller attacks can be mitigated with firewall rules, this allows for very fine scrubbing at minimal cost.
Filtering and mitigation have 3 layers of protection:
- FlowSpec firewall rules on Juniper MX204 to drop or rate limit traffic.
- Chelsio 2x40GE cards on Filter servers to drop or rate limit traffic.
- Blackhole routing as a last line of defense, for any traffic which is outside of available bandwidth.