Few details about both methods to capture traffic and the impact on network equipment.
Before tackling DDoS protection first thing to consider is – How we will collect data?
Will it be NetFlow / IPFIX or direct traffic mirror. This should be taken into account, as each choice gives You some limitations and advantages over the other one.
If your device has no more free ports or the NetFlow doesn't run as expected, you might consider an alternative approach - passive or active optical tap. Here are some examples of devices:
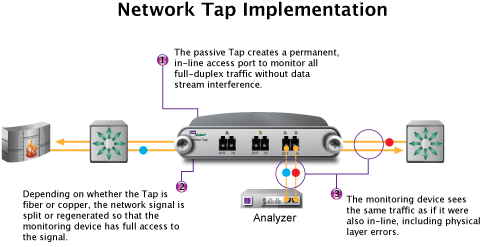
Below is as simple breakdown for and against each choice:
Mirrored Traffic
| + Pros | - Cons |
|---|---|
| 100% visibility, no delay | Traffics is copied RX+TX ( 5Gb\s + 5Gb\s TX) |
| 100% passive flow | Some restrictions apply with many ports/vlans etc |
| Less strain on switch/router | Additional ports and cabling required |
NetFlow / IPFIX /sFLOW /jFLOW
| + Pros | - Cons |
|---|---|
| Only available option for big telcos, as there is too much bandwidth on links | Sampling rate n-th (Visibility) |
| Easy to setup on devices which operate at layer 3 | Resource-hungry |
| No cabling required | During attack there are small errors in detection * |
| More options to configure: flow timeout, active/inactive flow time etc. |
*Explanation for error detection during attacks
According to Cisco Live BRKSPG-3335 presentation by Nicolas Fevrier, Rajendra Chayapathi and Syed Hassan „DDoS Mitigation Deployment - Impact on your Architecture”
The Variation of Sampling rate have little impact on ability to detect the attack, althou there are some small errors in detection.
Generic Flood Attack (84B packets, distributed attack of 100Mbps per router interface)
| Sampling | Error |
|---|---|
| 1:1000 | 2,1% |
| 1:2000 | 2,9% |
| 1:4000 | 2,9% |
| 1:10000 | 6,5% |
Summary:
Generally speaking traffic port mirroring is much better both for Your Wanguard analysis and network devices. If you can spare some ports, then You can defend against very short and pulse attacks (less than 30 seconds).
With recent development of Wanguard 7.0 there are many options for packet capture engines:
| Capture Engine | Speeds | Cost | Complexity |
|---|---|---|---|
| Embeded LibPcap | 1-4 Gb\s | 0 | none |
| System LibPcap | 1-4 Gb\s | 0 | none |
| Myricom Sniffer 10G | 10 Gb\s | 270 USD per card | |
| PF_RING | 10/40 Gb\s | 150 EUR per mac | Additional kernel driver / medium |
| Netmap | 10/40 Gb\s | 0 | Additional kernel driver / high |
| DPDK (experimental) | 10/40 Gb\s | 0 | Additional kernel driver / high |
If You have a bigger network and You can’t afford to mirror every WAN port – then you have 2 choices NetFlow or sampled traffic.
Using this method router will sample 1/10 packets and send it to Wanguard, this way from 30 Gb\s we can cut our traffic to 3Gb\s.
Since every network is different the approach must be individual. Your main focus here is the types of attack and network bandwidth to be considered.
If You have trouble deciding , please contact us to pick the best method for You.
Additional information:
Below are some link for Cisco / Juniper switches and additional information to take under considerations before deploying Your Wanguard
Cisco NEXUS 3000 SPAN Configuration and limitations (NXOS 7.x)
